The purpose of lab 4 imaging and hashing to show the user how hash values are be used to authenticate document and duplicated digital images. Also, to see how small changes in data show changes in hash values and last but not least to verify the image came from the right source by using hash values to check the result.
Introduction
The steps in be and become a forensics investigation are to preserve and duplicate digital content. For example document, email, image, and files on a computers and mobile devices. In lab we will used 4GB flash drive this is one type of media, this lab we will show a static type digital storage device.
Verification of authenticity of files
In computer forensics investigations need to make sure that the data collected must be authentic and accurate or else the evidence is useless. To proof files are valid and original many forensics investigations used hash value. Hashing is a digital fingerprint of a file, partition, or entire hard drives and can be used to detect malware. In addition, forensics investigations have to think if evidence is plug into to another computer without block mount it will change the original evidence.
Task 1: Acquiring Hash Values of Files
- We created a file name hash1 which end the extension .txt open it and type the phrase “Computer Forensics Investigation is fun and challenging.”
- Save the file and create two more files with the same content the file names should be hash2 and hash3. At the moment all three files should have the same content.
- Which mean all files should have the same hash value at this moment if we run the program hashmyfiles.exe.
- In file name hash3 change the phrase to “Computer Forensics investigation is fun and challenging.”
- This is a very small change to the another notepad documents.
- We will see if this change the hash value by using the program hashmyfiles.exe.
- We download and unzip the hashmyfiles.exe program.
- This program hash in ways there are MD5, SHA1, and CRC32
- The result the first two hash1 and hash2 have the same hash values, but hash3 have a different hash.
- A small things in the files have big differences in the hash value.
- The reason three files have different names, but the first two files still had identical hash values because hash values don’t go by file name but the content inside the file. For example even though the first two files have the different names but the content was the same but in the hash3 the content just little which completely change the hash values.
Task 2: Image using FTK Forensics Toolkit
- FTK Imager is imaging tool to image your USB flash drive.
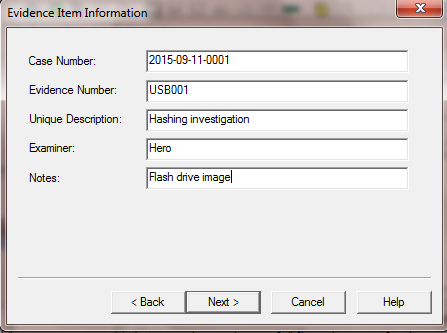
- This image above represent is building a case which is described as 2015-09-11-0001” for Case Number, “USB001” in the Evidence Number field, “Hashing investigation” for Unique Description, “Hero” for Examiner, and “Flash drive image” for Notes.
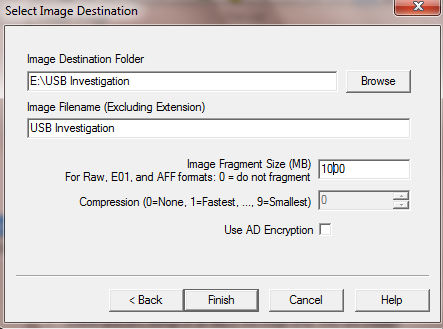
- We are setting the image fragment size which it going to be 1000 MB.
- If the USB flash drive is only 4GB it should only take about 5 minutes to complete, but if it bigger it will take a longer time to complete.
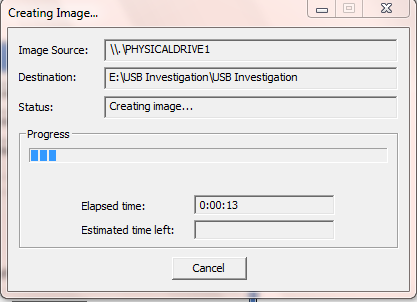
- This is showing the imaging in progress.
- Upon on completion a window will appear giving us a detail information about the image created. It will create five files with the name USB Investigation.
- Record that hash value is the image above.
- Yes, the log do shows the original and the image match basic on the image above after completing the imaging.
Task 3: Load the Image in FTK Imager
- From program can view the file USB Investigation.001 and check the content of recently deleted files as well as check if a files content have been modified.
- This tool is used to load the image, and view data this method prevents change evidences.
- The way we take hashing process and apply it to computer forensics is by making sure that data is accurate and original and detect any change within the data.